Built to protect your data and your trust
End-to-end security designed for institutional standards

Control and auditability
Role-based access controls let you manage who sees what. All platform activity is logged for full traceability.

Enterprise-grade hosting
Our infrastructure is hosted on secure, industry-standard providers with 24/7 monitoring, DDoS protection, and failover systems in place.
Encryption
All data is encrypted in transit (TLS 1.2+) and at rest (AES-256). Sensitive access tokens are never stored in plaintext.
Customer testimonial
“Evertrace has further streamlined our sourcing processes and made our setup even more scalable. It has helped us reduce the manual workload and improve our ability to identify new founders, particularly in countries outside our core markets. It has been a valuable enhancement for us.”

Any questions?
Find answers below
Yes. You can create team accounts and assign roles (e.g., Owner, Admin, Member). Features like saved searches can be shared or kept private as needed.
We store third-party access tokens encrypted at rest using AES-256-GCM. Tokens are scoped to the minimum required permissions and can always be revoked.
We don’t store user-generated passwords, as sign-in uses magic links (email-based one-time tokens).
We log specific usage statistics to enable product optimization - logs exclude plain text access tokens and similarly sensitive information
Yes. You can request deletion at any time, and we will remove your account and associated personal data from our systems.
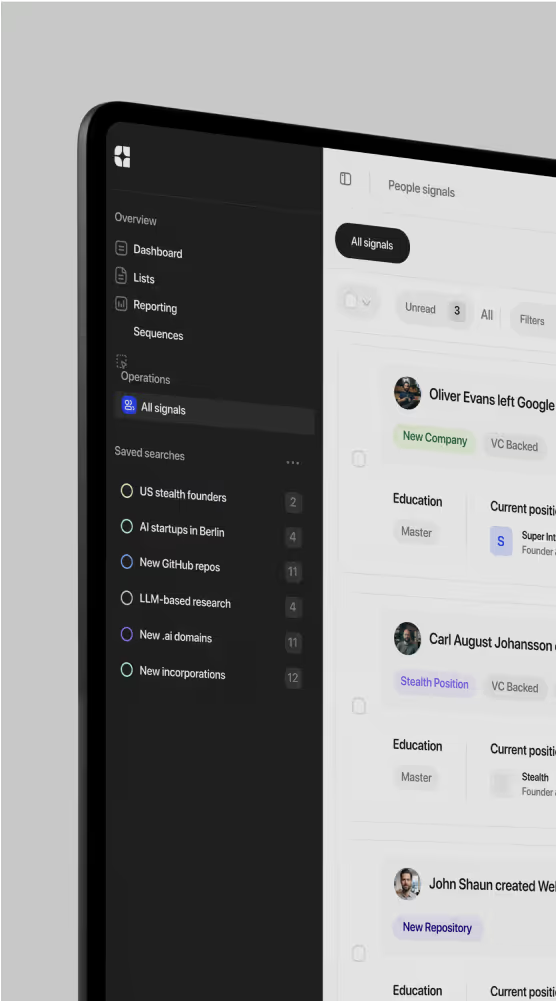
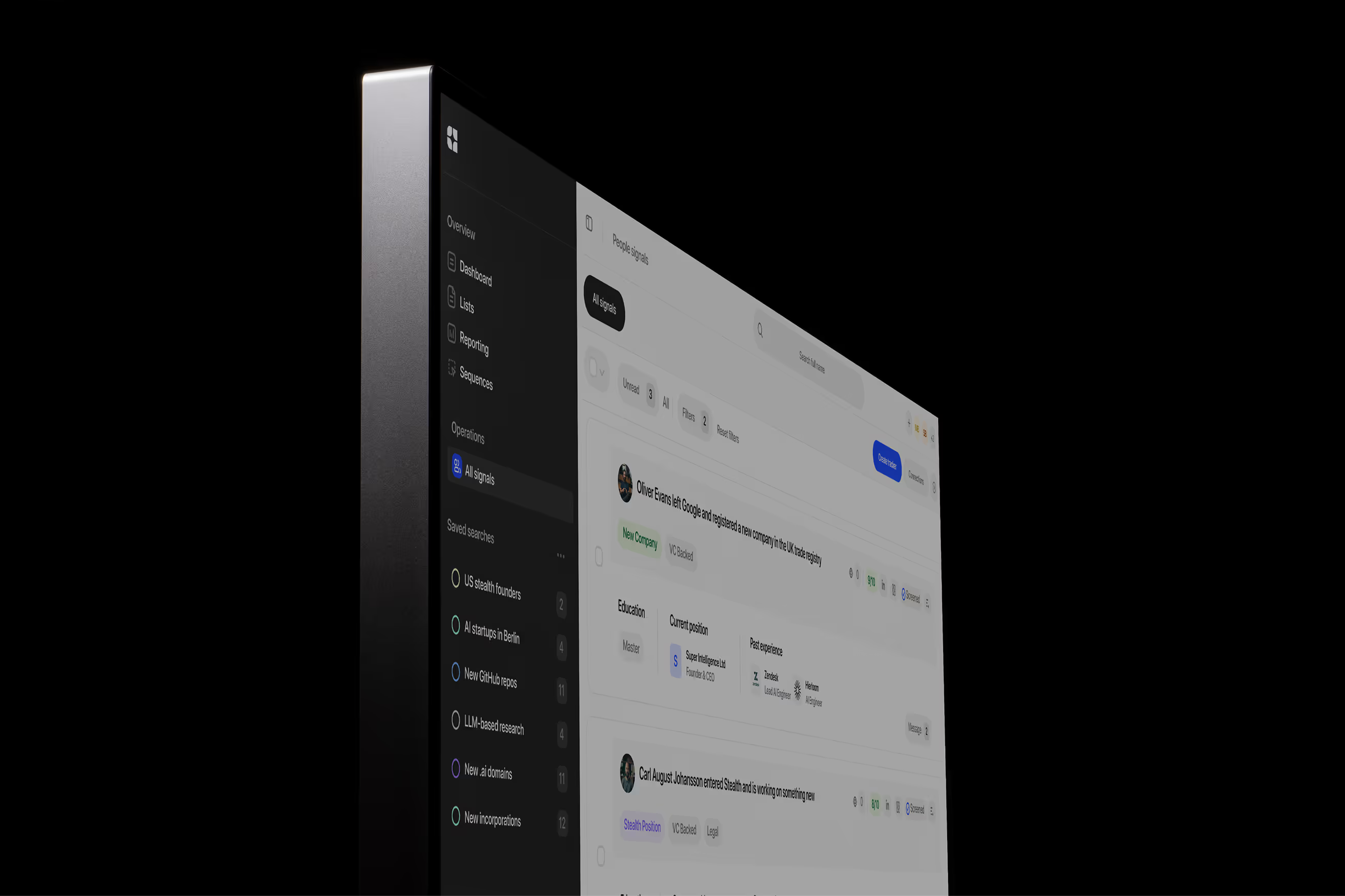
Get clarity from chaotic signals
We’ll show you how we structure fragmented data into actionable insights
— across code, social, IP and much more.